Why the Carbanak Campaign and the Bangladesh Bank attacks are a wake-up call for every AML compliance program.
Someone once asked me how long will criminals continue to find new ways to circumvent money laundering laws. My reply was simple, so long as crime is profitable they will continue to innovate to avoid AML laws and bank procedures. For any company, survival means consistently adapting to new economic, geographic, and regulatory changes. Therefore, for those syndicates operating illegally the need to launder money will always be there.
If the market value for illegal trade was $650 Billion in 2011, one must wonder how many hundreds of billions are lying under mattresses around the world waiting to be launder. Nevertheless, the direct use of financial institutions for laundering money will be a much more daunting task as in the past. Employees are well trained to detect the threat of money laundering and terrorist financing. As well, regulators today cooperate globally to align, develop and promote an international response to combating money laundering and terrorist financing. AML laws are continually being amended, for example, know your customer(KYC) and beneficial owner rules have been strengthened in most parts of the world.
Therefore, we need to start thinking about a new scenario where organized crime syndicates start replacing conventional methods to launder money with more advanced methods where technology is the business enabler.
A summary of illicit markets and values
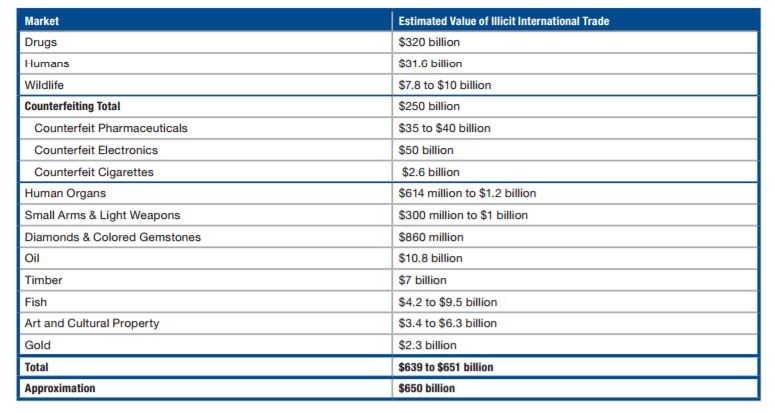 (Source: Transnational Crime In The Developing World February 2011 by GIF)
(Source: Transnational Crime In The Developing World February 2011 by GIF)
The Carbanak campaign and the Bangladesh Bank cases are the new normal in financial crime.
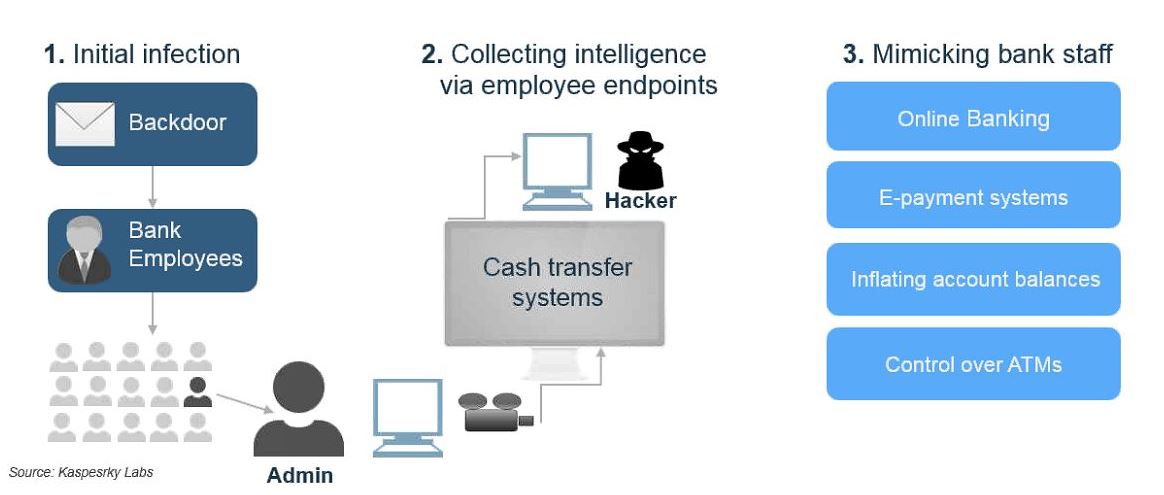
Let’s imagine a scenario, where cyber-attackers would exploit a vulnerability in a financial institution’s system. However, unlike other cyber-attacks, these hackers are not out to steal money. These cyber-attackers hired by an organized crime syndicate who have acquired money from illegal trade. Their mission isn’t to steal money from the bank but place dirty money in the bank(s) and immediately start layering (transferring) it through accounts at other financial institutions. By using sophisticated malware cyber attackers can enter the bank, learn internal procedures and then when ready takeover mission critical banking systems to start the layering process by transferring money to fake or real accounts. With control of the command server(s), they would easily bypass all anti-money laundering systems going undetected by bank officials. They would want to use the different time zones, regional and local holidays and business hours to their advantage.
A report by Kaspersky Lab in 2015, stating that over 100 banks around the world had been compromised to the sum of $900 million USD. It wasn’t detected until an ATM machine in Kiev started dispensing cash and this was no isolated event. The Carbanak malware was installed and sitting on the bank’s computer systems for months, conducting a reconnaissance mission of how the bank carried out business critical tasks. This international group of hackers was then able to successfully impersonate bank officers and carry out internal procedures at over 100 banks around the world. With complete control of mission-critical systems, they turned on various cash machines and managed the transfer of millions of dollars from banks in Russia, Japan, Switzerland, the United States and the Netherlands into fake bank accounts set up in other countries.
The Carbanak Campaign:
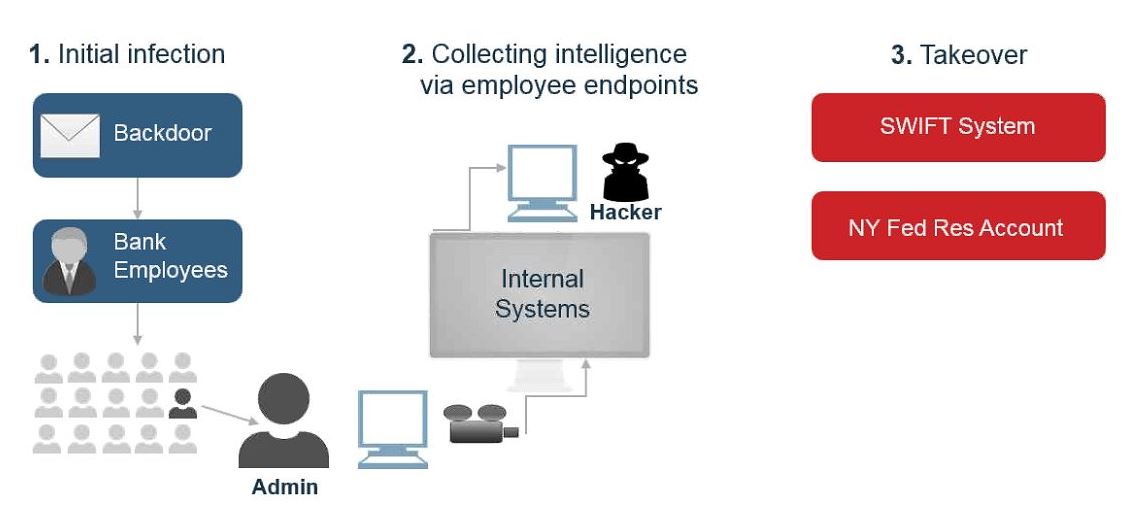
The February 2016 cyber attackers illegally transferred (steal) US$951 million from Bangladesh Bank, the central bank of Bangladesh, to several fictitious bank accounts around the world, via the SWIFT network. This was without questioned a well-planned attack and the way regional holidays and time difference were used was brilliant.
The Bangladesh Bank Campaign:
There has been much debate as to whether cyber and anti-money laundering units at financial institutions should remain distinct entities. Everybody agrees that efforts to share intelligence between the units should be ramped-up but would this will be enough. One of the biggest problems for large financial institutions when it comes to combating fraud and anti-money laundering is everything operates in silos. In a digital era, with people connecting to financial institutions from multiple devices and locations. It’s no longer an option for financial institutions to operate in batch mode when it comes to financial crime. The dots need to connect in real-time or you lose.
It’s only a matter of time when organized crime syndicates start to launder money per the “What If” scenario or they already are, who would realize it since nothing has been stolen and all records deleted!

Paul Hamilton
Group moderator
Paul Hamilton is a business development specialist for financial technology. After playing professional basketball in Europe, his focus turned to financial services and ultimately to financial technology where he won 15 years of experience working for global players, an SME and a start-up. His enthusiasm and excitement for developing new market opportunities have always been his passion going as far back as his first job as a broker selling investment products. Since then, he has worn many hats and as a consultative sales person, he has worked with financial service providers across EMEA and Asia to help them achieve their business goals.
Paul is also group moderator and founder for the financial crime blog site AML Knowledge Centre. To read his and member blogs go to http://aml-knowledge-centre.org/ or alternatively, you can join the AML Knowledge Centre at LinkedIn https://www.linkedin.com/groups/8196279
Paul enjoys connecting with people so if you want to talk about business, financial technology, or sports and fitness, he’s your person:-)



