Cybercriminals predate the use of cryptocurrency
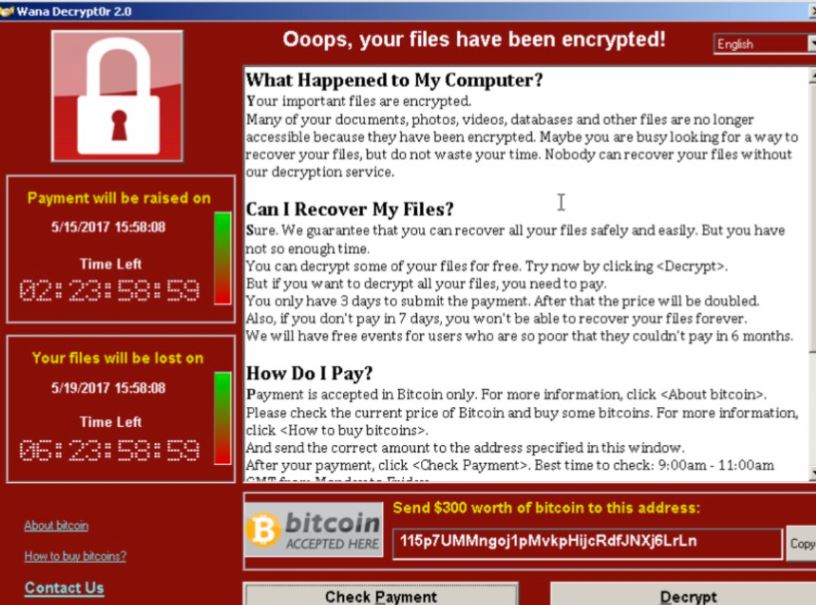
Indeed, editorial stories like this one “Bitcoin Gains Value Due to Criminal Use [Only], writes a Forbes Columnist” has influenced many into believing that cryptocurrency is only used by cybercriminals, organized crime and terrorist on the darknet. Before cryptocurrency, victims were informed to transfer ransom money by mailing cash through a money transfer operator (MTO). The pick-up person using fake documentation would take possession of the victim’s cash, leaving no trace of their real identity.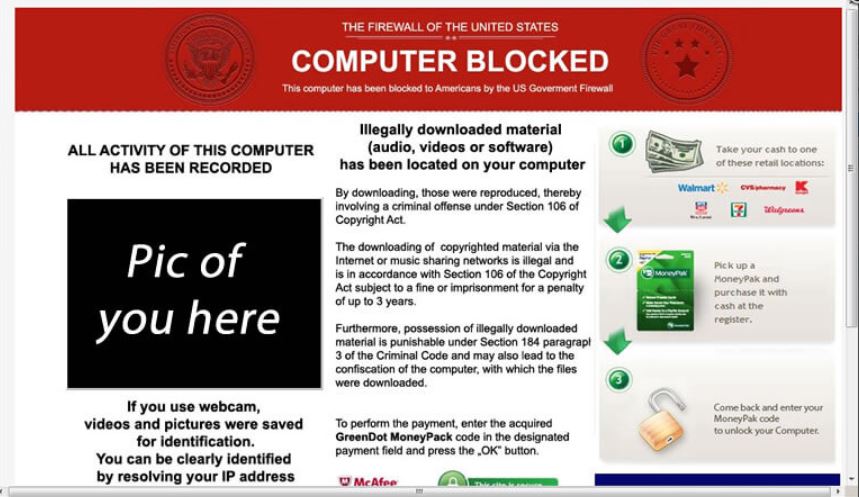 Victims of the WannaCry ransomware attack, in May 2017, received a simple message informing them to send $300 worth of bitcoin to this address if they want to see their data again.
Victims of the WannaCry ransomware attack, in May 2017, received a simple message informing them to send $300 worth of bitcoin to this address if they want to see their data again.
 Criminals continue to evolve by exposing any method or means available to them including technology. However, using cryptocurrency doesn’t put criminals out of law enforcement’s reach. On the contrary, as soon as a cryptocurrency is spent, the forensic trail begins. This is an excerpt from the book Cryptocurrency Modern Day Payment System or Uncalculated Risks? Which can be read on Amazon Kindle Unlimited for Free
Criminals continue to evolve by exposing any method or means available to them including technology. However, using cryptocurrency doesn’t put criminals out of law enforcement’s reach. On the contrary, as soon as a cryptocurrency is spent, the forensic trail begins. This is an excerpt from the book Cryptocurrency Modern Day Payment System or Uncalculated Risks? Which can be read on Amazon Kindle Unlimited for Free
The Forensic Trail Begins
Maybe, law enforcement panicked in the beginning, but they have adapted to cryptocurrency and their blockchain technology. Granted, cryptocurrency transactions themselves are not tied directly to anyone’s identity, but every transaction uses a unique string of letters and numbers 1Ez69nzzmePmZX3WpEzMKTrcBF2gpNQ55, that recognize the destination of both sender and receiver. These unique strings of letters and numbers give law enforcement enough information to follow transactions on a blockchain and eventually to a recipient’s e-wallet. More importantly, than the information itself is that all of a blockchain’s data is traceable, permanent, immutable, reliable and available to everyone who wants to see it. Therefore, that line “follow the money” made famous in the 1976 motion picture “All the President’s Men” is as true today as it was then. Not only a digital time stamp but a digital witness!Techniques and Tools
Like criminals, law enforcement has adapted to these new technologies developing new techniques and tools to follow and identify cyber attackers, even on unused addresses. Agents monitor blockchains and the darknet looking for correlations across transactions and their attributes such as:- Timelines
- Amounts
- Domain names
- IP and email addresses
- Pseudonyms
- Payments
- Connections
- etc.
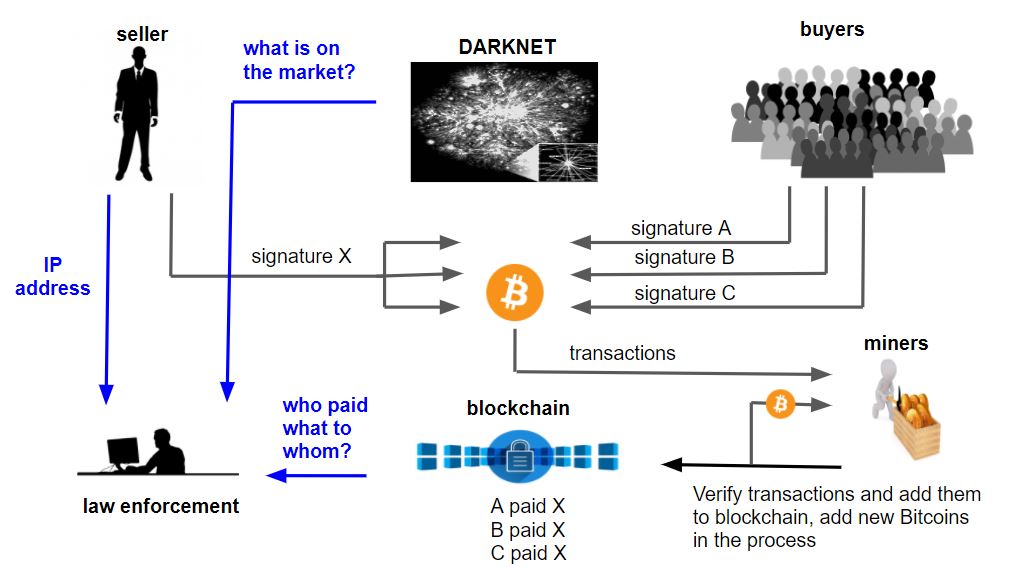 This analysis can lead agents to exchanges, e-wallets, and even gambling sites, on which law enforcement could serve a subpoena to learn more details on the transactions and the account owners. Once the payment recipient is identified, the investigator will have a confirmed IP address, location as well as a criminal profile, potentially linking a suspect to other criminals and crimes.
This analysis can lead agents to exchanges, e-wallets, and even gambling sites, on which law enforcement could serve a subpoena to learn more details on the transactions and the account owners. Once the payment recipient is identified, the investigator will have a confirmed IP address, location as well as a criminal profile, potentially linking a suspect to other criminals and crimes.
Consider this before Going the Extra Mile
For those, individuals willing to go the extra mile to cover their tracks. The market is saturated with unlawful businesses offering alternative entry points and mixing services to help users improve the anonymity of their cryptocurrency transactions. Likewise, there are cryptocurrencies like Monero (XMR), DASH (DASH), and ZCash (ZEC) that offer users an extra layer of privacy by applying zero-knowledge proof or a built-in mixing process as is the case with DASH. Granted, the options for concealing one’s identity are endless and as a result, it makes life harder for law enforcement to follow or tie a transaction to an individual, but not impossible! Before deciding to use an alternative entry point or a coin with zero-knowledge proof to hide one’s identity here are some things to consider:- Cyberattacks and insider fraud are not uncommon events at legitimate cryptocurrency businesses. I can’t imagine that an unlawful business would be a better custodian for someone trying to hide the source of their money.
- A majority of businesses operating unlawfully are already on law enforcements’ radar and a subpoena can be issued at any time.
- A business offering unlawful services can also be a setup by law enforcement.
- Mixing is more vulnerable to Sybil attacks.
- Mixing is not immune to forensic technology so there is always a real chance that investigators can link the coins back to the original address.
- Mixing needs at least two people, therefore you are helping someone to launder their money
- What if, after mixing, you receive coins that were involved in a crime and law enforcement traced them to you. Likely outcome these coins will be confiscated and you might require expensive legal counseling to avoid criminal charges.
- Let’s not take our eyes off the main players in the industry. Miners confirm valid transactions. Also, 50 percent of the hashpower is controlled by a handful of miners. Government agencies can always apply pressure to these miners as witnessed in China.
- Coins that claim to offer total privacy all have their own nuances and if not used accordingly can jeopardize any chance of anonymity. For example, take Monero it offers users full anonymity as long as it is used on its blockchain. Also, many are relatively new ICOs, therefore, the bugs haven’t yet been identified.
- It’s only a matter of time before the crypto-industry is regulated and it’s probably safe to say that holders of coins offering total anonymity will be penalized.
- Unfortunately, for bad actors, the flow of sending and receiving data through these cryptocurrency networks are not well-coordinated events. Therefore, anyone monitoring a network will be able to immediately recognize when a transaction is sent out and map it to that IP address as the owner of that cryptocurrency. Also, when a massive number of transactions are sent from a single source, it’s only a matter of time before the addresses are unwound and mapped to their proper IP addresses.
“Top Misconceptions of Cryptocurrency as a Payment System”
 Which can be read on Amazon Kindle Unlimited for Free You can find more interesting articles by visiting us on one of the following platforms: AML Knowledge Centre (LinkedIn) or Anti-Bribery and Compliance at the Front-Lines (LinkedIn)
Which can be read on Amazon Kindle Unlimited for Free You can find more interesting articles by visiting us on one of the following platforms: AML Knowledge Centre (LinkedIn) or Anti-Bribery and Compliance at the Front-Lines (LinkedIn)


