How is Blockchain Being Applied to Cybersecurity Right Now?
We’re getting pretty used to hearing about cool new projects using blockchain. From online marketplaces to green energy; every man, woman, and their respective dogs are busy leaping on the bandwagon. Future promises, flashy launches, impressive white papers… These things are all well and good. But what about practical use cases happening now, starting with cybersecurity?
Blockchain and Cybersecurity
Whenever you talk about the blockchain, you almost always enter a discourse of hypotheticals. This is true in relation to government and commerce, and it’s true of cybersecurity as well. But cybersecurity is a pressing problem, costing the global economy an estimated $450 billion a year.
So, rather than speculate over how blockchain may eventually resolve the woes of this problematic industry, what problems is it tackling now? And which companies are getting their hands dirty (so to speak)?
“Blockchain has plenty of genuine use cases,” says Nick Bilogorskiy, Cybersecurity Strategist at Juniper Networks, “for example decentralized storage, preventing fraud and data theft, and distributed public key infrastructure for user or device authentication.”
Multi-Factor Authentication
DDoS (Deliberate Denial of Service) attacks are one of the most common cybersecurity threats in the industry today. And they are rampant and widespread mainly due to our existing Domain Name System. When we hold data in one centralized location, it’s infinitely easier to break into. With blockchain’s decentralized structure, distributing information over nodes, systems will become virtually impossible to hack.
“Instead of all passwords of users being held in one database in the network operations center of one company, each individual holds their private key,” says Nick Spanos, founder of the Bitcoin Center NYC. “Companies like Equifax and Wells Fargo would never again handle information the way that they did. You would have to hack millions of their users simultaneously–a much more difficult feat.”
Winner of the Microsoft Blockchain Incentive award, blockchain security startup REMME is currently preventing cyber attacks on companies large and small. By eliminating the room for human error, and the simple one-step password system widely used, we close the window for opportunist hackers scouring for easily crackable passwords.
REMME’s robust solution is built on the decentralized ledger and manages and authenticates users and devices through multi-factor authentication. This eliminates the chances of preying on the easiest target for cyber attackers (weak passwords).
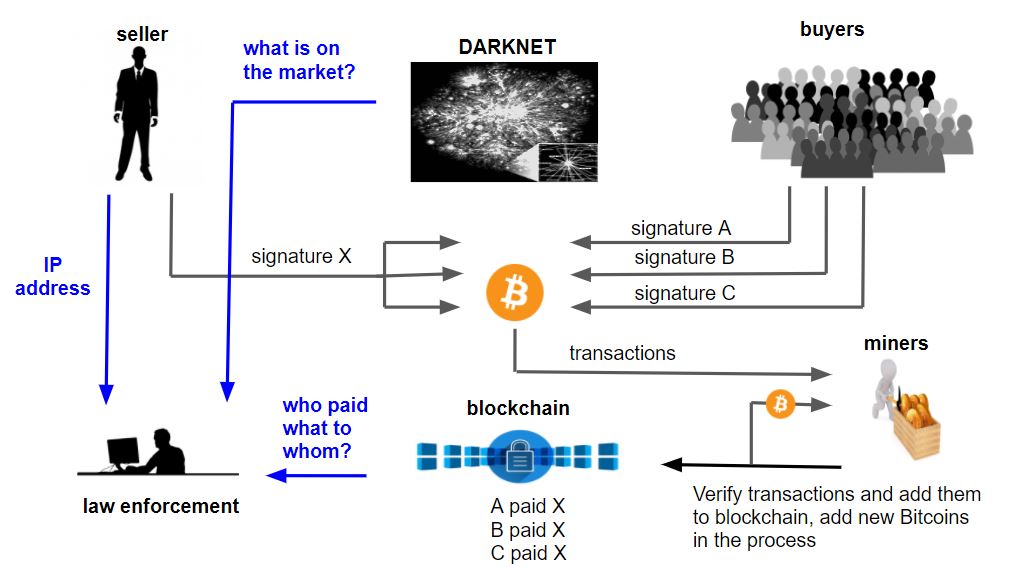
The company is also working with several Bitcoin exchanges to help prevent phishing attacks like the Bitfinex attack that lost $60 million (120,000 BTC at the time). They provide the security of an authorized platform based on cryptographic principles and a user-friendly, one-click 2FA.
Improving IoT Security
One of the stumbling blocks in the road of IoT’s growth is the constant threat of device security. According to research by Gemalto, 96 percent of companies and 90 percent of consumers believe that their IoT devices aren’t secure–and that there should be government regulation in place. Their main concern, it seems, is that a hacker will take control of their device, or that their personal data will be stolen.
When baby monitors and medical devices are infected with Malware, and major car manufacturers lose control over their vehicles, the public’s concern is understandable. The thought of losing control of your car or respiratory equipment is indeed panic-inducing. But here too, blockchain is starting to show some results.
IBM has a long history of innovation. So it’s not surprising that they’re leading the charge when it comes to blockchain tech. The IBM Watson IoT Platform is allowing IoT devices to transmit data to blockchain ledgers. This data is then included in shared transactions and records that are tamper-resistant and validated through secure, smart contracts.
Australian telecommunications giant Telstra is also seeing success using blockchain to secure their “smart home” IoT ecosystems, by verifying people’s identity through stored biometric authentication data. And IOTA is also showing promise for the scaling of IoT through its Tangle technology.
Filling the Talent Gap
You may have thought there were more than enough computer engineers to go around. But it turns out that there’s quite a talent shortage when it comes to cybersecurity.
Unemployment in the industry hovers around zero. This means that when new positions crop up, they are extremely hard to fill. And with the constant challenges of emerging tech (and with them, greater cyber threats) by 2020, Frost & Sullivan predict at least 1.8 million vacant positions in the cybersecurity industry.
Companies like PolySwarm, a decentralized antivirus marketplace, incentivize techies around the world to contribute toward fighting cybercrime. Not only does this give bright talent a chance to shine, regardless of their location, education, or history, but it also helps detect cybercrime faster.
Dwell times (the amount of time a virus sits dormant inside a system before activating) is one of the most serious threats today, meaning speed is of the essence. With former McAfee Antivirus CIO Mark Tonnesen as an advisor to the PolySwarm team, stopping cybercriminals in their tracks and preventing attacks is becoming a reality.
Not Everyone’s in Agreement
Of course, the debate about blockchain and its suitability as a technology rages throughout the cybersecurity industry as well. Despite the growing number of use cases and gathering momentum for blockchain, not everyone’s in agreement about its potential.
CEO of Gunner Technology Cody Swann says, “We’ve been inundated with requests for blockchain apps from entrepreneurs. Unfortunately, none of these products have made it past alpha on the blockchain. Why? Because in the vast majority of the cases, the blockchain is an inferior choice to most technologies.”
Worldpay Vice President and Head of Global Cyber Defense & Security Strategy, Peter Tran, is also less than enthused with blockchain technology so far. He believes that artificial intelligence and machine learning have the upper hand in fighting cybercrime. And also that rehauling existing infrastructures may not be an economic reality.
The challenge here will be in making blockchain technology easier, more effective, and cheaper to use. But it’s heartening to know that blockchain is already solving many of our problems and can only go up from here.
Originally published on Coincentral: https://coincentral.com/blockchain-applied-cybersecurity/
“Cryptocurrency Modern Day Payment System or Uncalculated Risks?” can be read on Amazon Kindle Unlimited for Free You can find more interesting articles by visiting us on one of the following platforms: AML Knowledge Centre (LinkedIn) or Anti-Bribery and Compliance at the Front-Lines (LinkedIn)
Author:
“Top Misconceptions of Cryptocurrency as a Payment System”
Which can be read on Amazon Kindle Unlimited for Free You can find more interesting articles by visiting us on one of the following platforms: AML Knowledge Centre (LinkedIn) or Anti-Bribery and Compliance at the Front-Lines (LinkedIn)