Money Laundering in a Digital Age – The Perfect Storm
The new Black
With the rapid advancement of mobile technologies, the internet is now accessible from any- and everywhere. Open banking (PSD2) in the European Union, together with mobile wallets, instance payment initiatives and cryptocurrencies offer consumers a lot of ways to engage with financial institutions 24/7. Therefore, in today’s environment, customer expectations are constantly changing and it’s imperative that financial crime and Anti-Money Laundering units keeps pace.
No doubt that the widespread use of mobile devices is accelerating the rate and impact of financial crime. Today, mobile subscriptions outnumbered the world’s population as illustrated by Statista:

Which in turn, has spurred the use of mobile banking apps and the way consumers pay for generic services, in general altering us into a cashless society.
With new regulations such as the Payment Services Directive (PSD2), the European Union has set the rules for open banking, allowing FinTechs access to traditional financial institutions’ systems and customer data. Everyone is a winner, the benefits of open banking are enhanced customer service for under-served markets, new revenue streams, and improved margins.
While this presents major opportunities for everyone it places a lot of responsibility on those tasked with keeping a financial institution from being compromised by cyberattacks or used as a vehicle to launder money.
How will current financial crime & anti-money laundering systems work in a digital world?
It’s difficult enough for financial institutions to monitor and detect violations of transactions taking at best 24 hours to clear. With digital payments clearing in real time the impossible becomes totally impossible using conventional methods as transactions clear in a matter of milliseconds. By conventional, we mean systems focused on a rule-based approaches, where suspicious transactions are put in a queue and investigated in an overnight batch mode.
Even in a world operating in batch, AML systems generate too many false positives (typically between two and 15% of all transactions) and therefore imposes a huge workload on banks and financial investigation units (FIU).
Number of Suspicious transactions reported to UIF in the UK: +51% (’12-16), from 67K in 2012 to 101K in 2016
As digital payments continue to increase, this problem is greatly scaled because banks are under pressure from customers and consumers to clear transactions as quickly as possible and still make sure that risk and compliance systems flag all risks and suspicious activities.
The Internet of Things
Once upon a time, cybercriminals focused their efforts on PCs. However, with the average user spending about five hours per day on a mobile device, with roughly 70 percent of those smartphone devices not having an anti-virus program installed on them, sensitive data (e.g. contacts, passwords, emails, documents, photos, etc.) are exposed to cyber threats. Therefore, we have witnessed a sharp increase in new mobile malware, because criminals will always take the path of least resistance.
The Internet of Things (IoT) is driving the interoperability of physical devices, vehicles, home appliances and other electronic equipment through sensors and software enabled apps.
The number of online-capable devices was believed to have increased to 8.4 billion by 2017 and by 2020 experts estimated that 30 billion objects would be online, with a global market value of $7.1 trillion.
The Nokia Threat Intelligence Report 2H 2016 estimated that more than 100 million devices worldwide have been infected by malware, including mobile phones, laptops, notepads and a broad range of IoT devices.
The same report stated that smartphones were more often targeted, accounting for 85 percent of all mobile device infections and smartphone infections increased 83 percent during July through December, compared to the first half of the year.
According to Check Point Mobile Threat Research’s 2017 report (“Mobile Cyberattacks Impact Every Business”) financial institutions, as the custodians of their customer’s money and data are a much sought-after target for cyberattacks. Malware attacks by industry:
With the number of mobile devices already infected and the connectivity of devices rapidly expanding, cybercriminals have more routes to target than ever before.
As crazy as it once seemed, cybercriminals attacking financial institutions via a coffee machine, smartphone or even an employee’s wearable health-check device is no longer science fiction. Also, this malware storm isn’t a regional threat but it’s path of destruction is universal. The most impacted regions according to Check Point mobile threat researchers:
Source: Check Point Mobile Cyberattacks Impact Every Business
The Eye of the Storm
That said, financial institutions appreciate the importance of digital technology and are embracing an ecosystem that includes FinTechs. These ecosystems can help to provide more customer value and open new customer segments. At the same time, they bring new types of operational risks with them, such as:
- Risky user behaviour. For example, 70 % of smartphone users have never installed an anti-virus program on their mobile device.
- 24/7 connectivity of mobile devices to hotspots.
- WI-FI networks and Bluetooth technologies making it easier for attackers to carry out a fraud campaign.
- Rogue mobile applications, repacking of apps and ransomware are on the rise.
- Advance malware & viruses for online as well as mobile devices continue to increase.
Currently, the data on mobile fraud isn’t as robust as with other channels. These operational risks need to be continually assessed to build reliable mobile fraud models without jeopardizing the customer experience. 60 percent of digital banking fraud originates from the mobile channel, according to figures published by RSA in 2018. This mobile banking fraud almost always involves thieves using RDC to deposit fraudulent checks, or cybercriminals using stolen identity credentials to hijack consumer bank accounts. This actually caused a dip in the growth of mobile banking as users sensed insecurity. Security and fear of fraud are the top two concerns about using mobile banking for up to 55 percent of consumers, according to Javelin Research. And with more than 25 million mobile devices infected by a single malware variant alone (Agent Smith) it is hardly surprising. The exact number of malware-infected mobile devices is hard to quantify, but in 2018 Kaspersky Labs and products detected:
- 5,321,142 malicious installation packages
- 151,359 new mobile banking Trojans
- 60,176 new mobile ransomware Trojans
A point often overlooked is that your ecosystem is the weak link when trying to protect against external threats. One lesson learned is the degree of difficulty to detect a compromise until bad things start to happen, examples:
The Carbanak malware set in the banks’ computer systems for months, sending back vital information to hackers, who were then able to impersonate bank officers carrying out internal procedures at more than 100 banks around the world.
With complete control of mission-critical systems, they managed the transfer of millions of dollars from banks in Russia, Japan, Switzerland, the United States and the Netherlands into fake bank accounts set up in other countries.
If not for a video surveillance camera filming an ATM machine in Kiev, the Carbanak malware might never have been detected.
From the US$ 81 million stolen from the Bangladesh Bank in February 2016 only US$ 15 million has been recovered and there is still no word on who was responsible. Cyber attackers illegally transferred US$ 81 million from the Central Bank of Bangladesh (CBB), to several fictitious bank accounts around the world, by subverting their SWIFT accounts.
The Bangladesh Bank heist is a perfect illustration of the future complexity involved in monitoring instant payments.
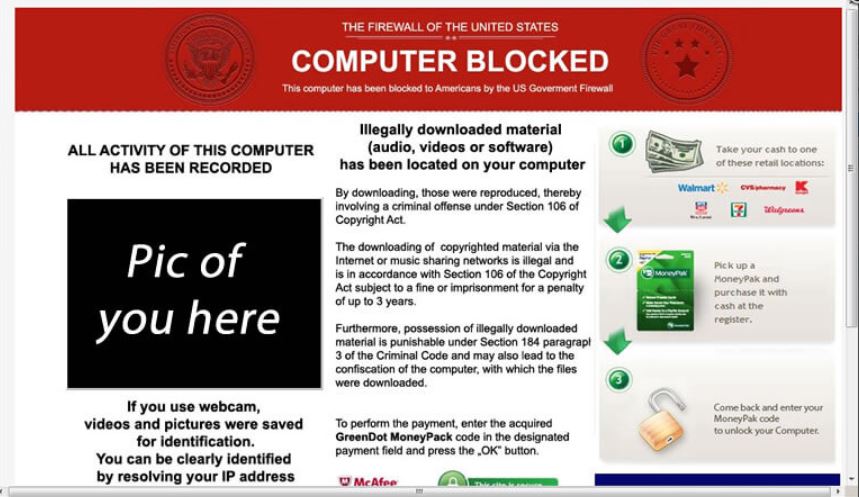
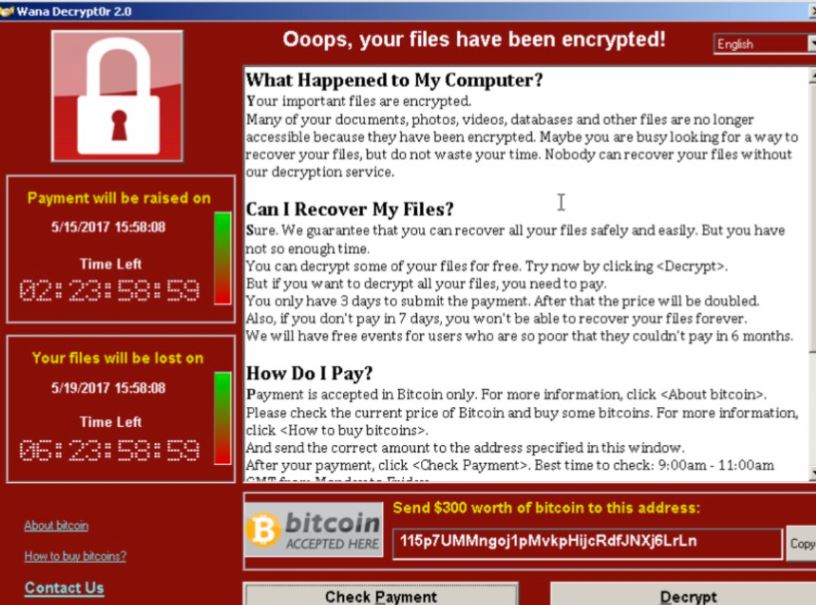
The WannaCry virus, quickly infecting more than 200,000 businesses in 140 countries. locking computers until a ransom was paid.
Fighting Back with Innovation
The only credible answers are detection and transaction monitoring systems built on new technology, with machine learning and artificial intelligence at the core and not relaying only a rule-based approach.
Criminals don’t use rules
Algorithms that continue to improve, with the support from financial crime and AML professionals, these systems learn to identify suspicious activity where there is a higher probability of a financial crime committed and/or money laundering actually occurring. Therefore, bank staff can focus on the real alerts and not get swamped down in false positives.
Another technology-based approach that continues to develop, provides insights by taking large amounts of account data and generating a visual map. Suspicious relationships and payments can be tracked as they move between bank accounts, regardless of whether the payment amount is split between multiple accounts, or those accounts belong to the same or different financial institutions. The software creates a visual map of where and when money has moved, providing new insights and intelligence for fraud and compliance teams to take action.
By bringing together transactional data from multiple financial institutions and running sophisticated algorithms, such solutions can identify the so-called “mule accounts” that are used for money laundering and other illegal activity. Many of these accounts are not set up directly by the criminals themselves but via a number of scams including phishing, spam email, instant messaging etc.
It is worth pointing out that while technology is a necessary condition for successful financial crime and money laundering prevention, however, it is not the only tool. In addition, financial institutions will need to review their compliance procedures, risk assessments, and their service offerings to strike the optimum balance between competitiveness and security.
What should be the upper threshold look like?
Should priority to VIP and profitable customers be given when reviewing suspicious transactions? What about social and political issues? (For example, Muhammad is the world’s most common name, and also appears a lot on sanctions list. But that also means a significantly large number of false positives, which could lead to claims of unfair profiling.)
And finally, even with advanced technology and effective redesign of processes and procedures is meaningless without a sufficiently well-trained staff to detect suspicious customer behaviour and be reliable gatekeepers, especially at on-boarding of new customers.
Author Paul Allen Hamilton
For more articles on financial crime and Anti-Money Laundering join the AML Knowledge Centre at https://www.linkedin.com/groups/8196279/