Disruption in the Financial Industry
Technology has always had the ability to generate hype and excitement. In addition, to the rising cost of risk and compliance executives are battling to drive more business value from these functions. However, the reality is these functions only support the business.
Exactly this prompted me to ask what, if any, impact is digital transformation having on risk and compliance functions at financial services institutions.
Before we deep dive into the digital transformation of risk and compliance, let’s look at where the financial services industry is in its digital transformation.
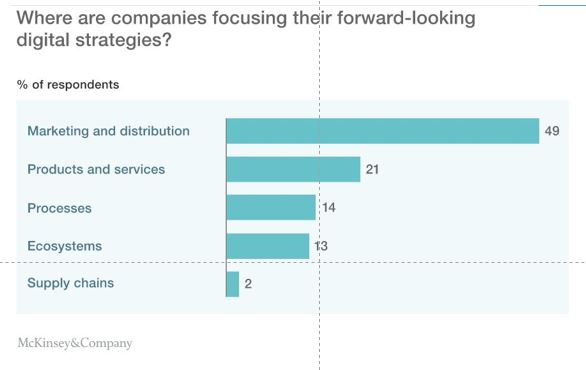
Despite the fathom rate of change that Fintechs have brought to the financial services industry. The industry on a whole is clearly lagging in digital transformation as pointed out in the graph by McKinsey&Company.
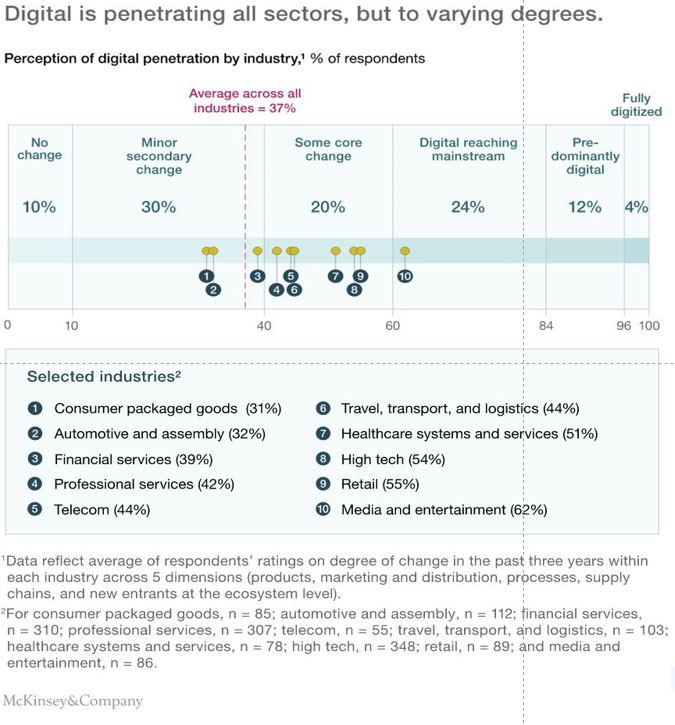
While a shift away from the historical product-centric mindset to a customer-centric e-commerce approach is a positive signal for customers. Many financial services institutions have yet to streamline and automate business processes as well as consolidate data sources across the enterprise and at all customer touch points. In the same manner as their e-commerce peers. Therefore, digital adoption in the financial services industry has been slower and lacking depth. As illustrated in the graph by McKinsey&Company.
Based on the change management history of the financial services industry, many would agree the people and process dimensions of digital business are the most difficult to transform. Of course, personalizing the customer experience is important to any digital strategy, but risk and compliance are paramount to the overall success of execution.
“Digital transformation is more than building cool customer apps or increasing the number of digital channels”
The Current State of Risk and Compliance
In recent Gartner surveys of CEOs across the globe, more than
77% of CEOs see digital business bringing new and increased levels of risk to their organizations. At the same time,
65% of the CEOs view their risk management investments and maturity as lagging behind their peers. Also, board members and senior management struggle to find intrinsic value in their risk and compliance programs and tend to view them as a cost of doing business. Why are CEOs and senior management responding like this? When hardly any industry spends more on technology than the financial services sector and a significant portion of that spend goes into risk and compliance technology.
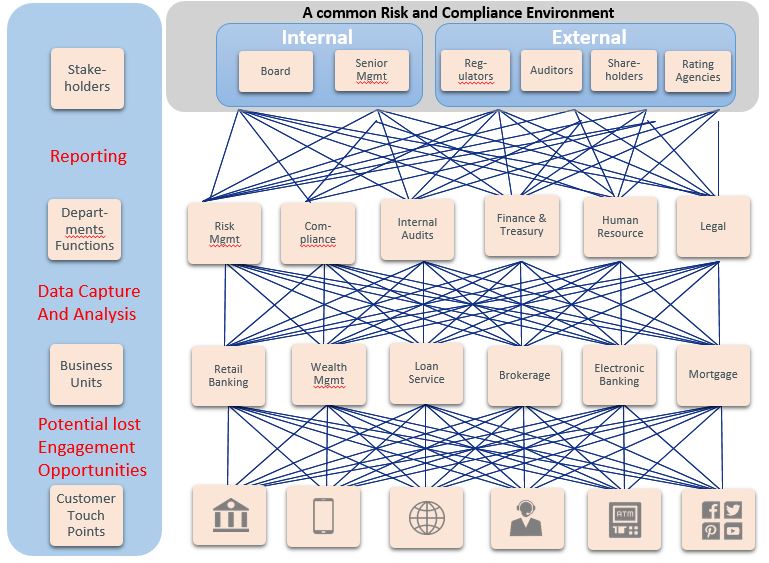
In a common risk and compliance environment, business units operate in isolation. Relying on decentralized data systems, and manual processes that are not efficient. This current environment does well to support the business, but not drive business value. Likewise, it’s costly to run and maximizes the
potential for lost engagement opportunities at most customer touch points.
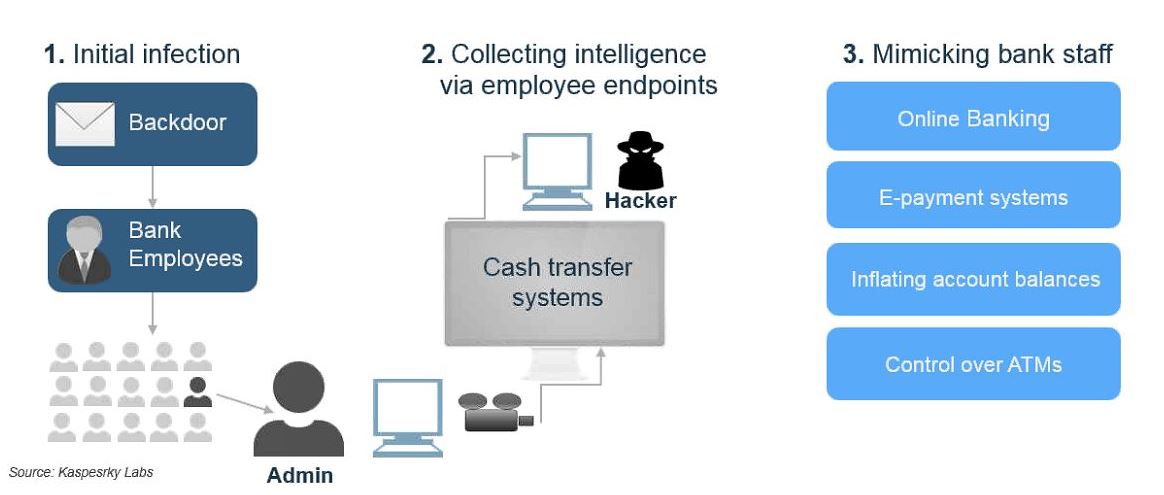
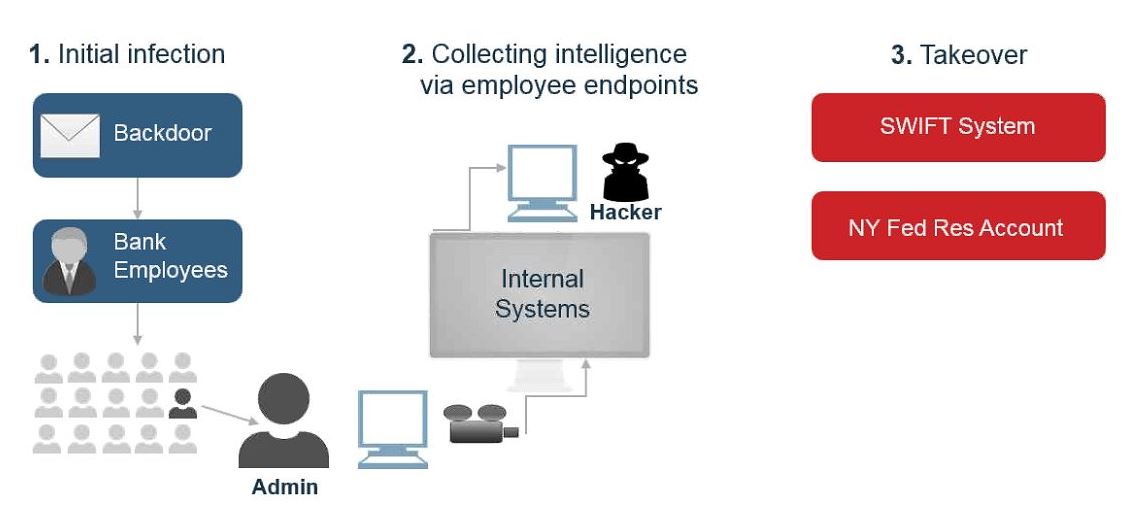
In addition to lost engagement opportunities, criminals thrive in this current state of complexity it offers them the perfect camouflage. In the Carbanak campaign, malware was installed on the bank’s computer systems, sending back vital information about how the bank carried out business critical tasks. Eventually, leaving
100 banks compromised to the sum of $
900 million USD. Highly fragmented IT and data architectures cannot provide an efficient or effective environment for monitoring, and analyzing risks in a real-time world while not disrupting customer transactions.
Driving the Business with a Customer-Centric Risk, and Compliance approach
AML/KYC
Today, customers expect real-time decisions at every touch point in order to complete their transactions. However, compliance can get into the way of transactions before they are completed. In fact, financial services institutions have endured a rough journey with AML. Their reward has been an enormous amount of false alerts, and a lot of manual processes.
For good reasons, compliance programs feel under-resourced compared to the volume of alerts and reports they must review, while trying not to disrupt good business. Therefore, many banks have invested massively in additional staff, to review false positive, while also turning away profitable high margin customers. As witnessed by massive lawsuits from Money Transfer Operators against banks trying to prevent them from closing their accounts.
The advantages that a Customer-Centric Infrastructure would have on an AML/KYC program:
- Learning transaction behavior of similar customers and clusters to accurately refine and update customer risk segments and individual profiles per their present risk.
- Identifying outlier transactions and outlier customers accordingly.
- Learning money laundering and fraud typologies and identify typology specific risks.
- Dynamically learning correlations between alerts which produced verified suspicious activity reports and those that don’t.
- Continuously analyzing false-positive alerts and learn common predictors.
- Many processes and workflows can be automated for example the KYC, controlling the initial screening of alerts, the filing of suspicious activity reports and parts of the case investigation.
- KYC process would no longer result in delays or potential loss of business.
In particular, streamlining KYC, AML, and Fraud processes at account-opening for a seamless onboarding will go a long way in improving customer satisfaction and ensuring new revenue. AML programs will become more efficient by automating workflow and incorporating technologies such as machine learning and advanced analytics that support the constant improvement of risk assessments and profiling models. This will free up resources and help compliance to go from monitoring to preventing financial crime.
Consumer Credit
As a result of low-interest rates coupled with sparse yields means banks generate fewer profits from the deposits they collect, against the loans they give. Therefore, to increase their return on consumer credit banks need to streamline and automate manual processes, improve risk assessments and stop credit fraud losses.
The advantages that a Customer-Centric Infrastructure would have to consumer credit:
- New integrated data sources, as well as unstructured data from social media, can give better insights into the creditworthiness of an applicant, therefore, protecting against fraud.
- Advanced analytics and machine-learning tools can increase the accuracy of credit risk models.
- New data sources, advanced analytics, and machine learning tools can help to detect inconsistencies between application, account and credit card transaction history.
- Learning patterns of similar customer behavior will go a long way to detecting fraud and money laundering.
In general, streamlining loan application processes to enable real-time decision making will improve customer retention, and be a decisive channel for winning new customers. Likewise, advanced analytics and machine-learning can increase the accuracy of credit risk models, therefore, reducing the time needed for structured credit approvals to a few minutes while minimizing a bank’s exposure to default risk.
Mobile Channels
Traditional banks are being challenged by FinTechs with new business models that are offering reduced fees and eliminating access barriers for the unbanked. As a result, this challenge has led to a major shift in the way money is moved around the world. Thus, breaking the dominance of banks in the area of payments. One good reason, the remittance industry accounted for
$583 billion, in cross-border payment transfers in 2014 and the World Bank expects the number to climb to
$636 billion in 2017.
With that said, digital technology is extremely important to the future of financial services industry. Therefore, traditional financial services institutions have embraced an ecosystem with FinTechs and third parties by allowing access to their infrastructure through APIs.
Although, these ecosystems can help to provide more customer value or open new customer segments. At the same time, they bring new types of operational risks with them, such as:
- Risky user behavior, especially with a mobile device. For example, 70% of smartphone users have never installed an anti-virus program on their mobile device.
- 24/7 connectivity of mobile devices to a network.
- WI-FI networks and Bluetooth technologies making it easier for attackers to carry out a fraud campaign.
- Rogue mobile applications, repacking of apps and ransomware are on the rise.
- Advance Malware & Viruses for online as well as mobile devices continue to increase.
“43% percent of merchants in one survey were not able to report what percentage of fraud losses came from their mobile channel”
Currently, the data on mobile fraud isn’t as robust as with other channels. These operational risks need to be continually assessed to build reliable mobile fraud models without jeopardizing the customer experience. In fact,
43% percent of merchants in one survey were not able to report what percentage of fraud losses came from their mobile channel.
Per a 2014 report from Alcatel-Lucent’s Motive Security Labs,
16 million mobile devices worldwide are infected with malware. A point often overlooked, is the fact that your ecosystem will make it more difficult for you to protect against external threats. One lesson learned from the Carbanak campaign is the degree of difficulty to detect a compromise until bad things start to happen.
A Customer Centric Risk and Compliance Infrastructure
Marketing and sales have been using customer loyalty, and customer-centric tools for years to effectively maximize sales and measure customer satisfaction. Leveraging sophisticated analytics and CRM tools to conduct market analysis, profile and segment customers to present them with offerings that best address their requirements.
It’s clear moving from a state of supporting the business to one of driving it is as much about people and processes as it is about technology. However, true success relays on data quality. Thus, buy-in from stakeholders is mandatory for a data strategy that establishes strong data governance and maintains the highest data quality built around a robust data architecture
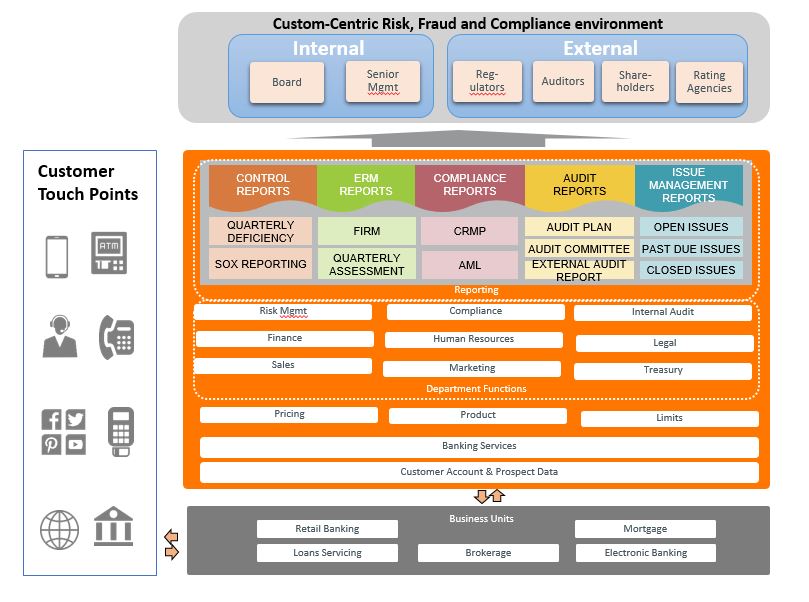
The cornerstone of the customer-centric risk and compliance architecture is a big data platform, advanced analytics, artificial intelligence, machine learning, workflow automation, and natural-language processing.
Not only can the platform aggregate and analyze all data from account and credit card transaction history but also check for inconsistencies between an application with both structured and unstructured data sources. Another plus of this architecture is employees have accessibility to one source of the truth. Therefore, minimizing the uncertainty of unknown risk-levels of exposures to financial & debt markets, counterparty, private credit, compliance risks, legal liabilities, and security threats from adversaries.
One survey stated that compliance was mentioned by
47% of participants, as the most mentioned obstacle to impeding their digital maturity thereafter fragmented data sources at
44%. By leveraging a customer-centric risk, and compliance architecture financial services institutions will drive its ability to mature digitally at a much faster pace.
Although the rewards are great when decisions are being made in real-time there is little margin for error. That said the journey will continue to be a laborious one for those who stay on the same path they started on. My profession international business development and sales are also my passions. Devoted to helping financial service institutions choose the right technology for their AML programs making them more effective and customer centric. An ex-professional basketballer with a passion for fitness and respect for nature. I enjoy starting inspiring discussions with articles on Anti-Money Laundering, Cryptocurrency, financial technology, Human trafficking, and terrorist financing as well as on sports & fitness. So, visit me at http://aml-knowledge-centre.org/ or http://sports.fastbreak-marketing.com/ or let’s connect on LinkedIn if you would like to discuss a topic…
My profession international business development and sales are also my passions. Devoted to helping financial service institutions choose the right technology for their AML programs making them more effective and customer centric. An ex-professional basketballer with a passion for fitness and respect for nature. I enjoy starting inspiring discussions with articles on Anti-Money Laundering, Cryptocurrency, financial technology, Human trafficking, and terrorist financing as well as on sports & fitness. So, visit me at http://aml-knowledge-centre.org/ or http://sports.fastbreak-marketing.com/ or let’s connect on LinkedIn if you would like to discuss a topic… auch gerne auf Deutsch:-)




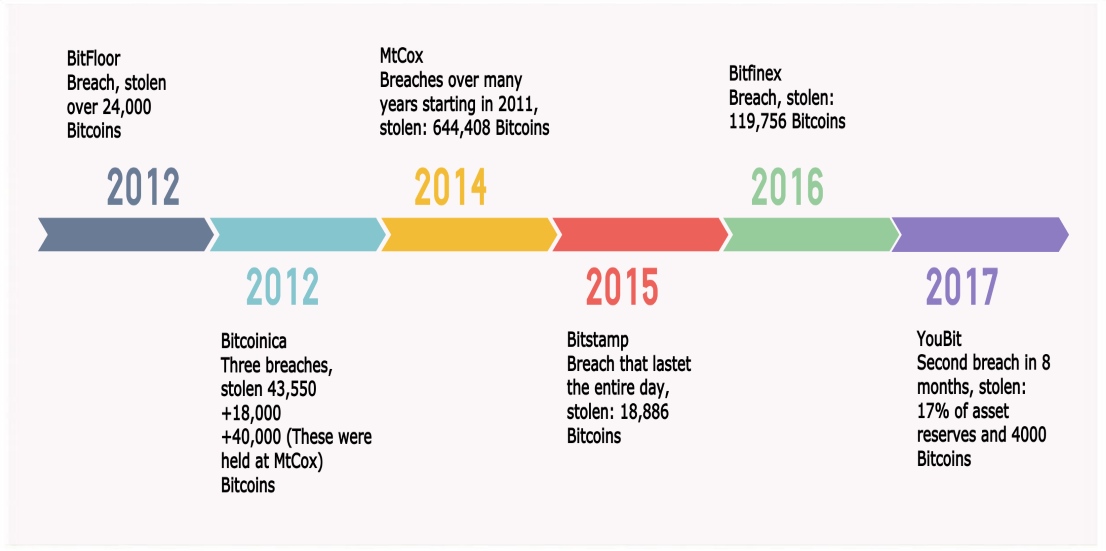

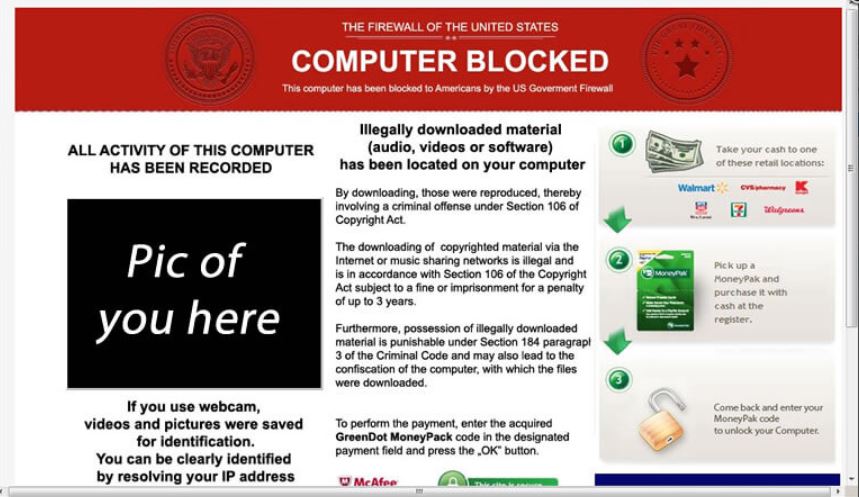
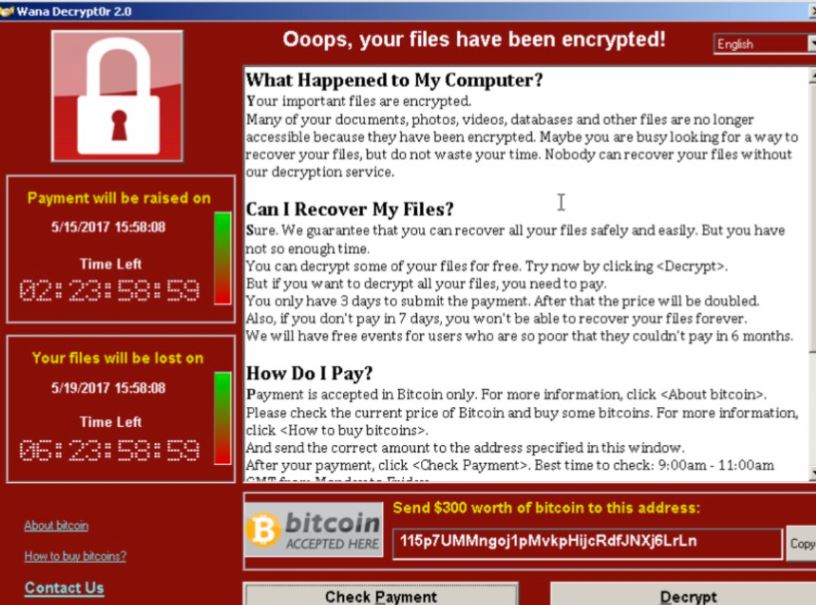
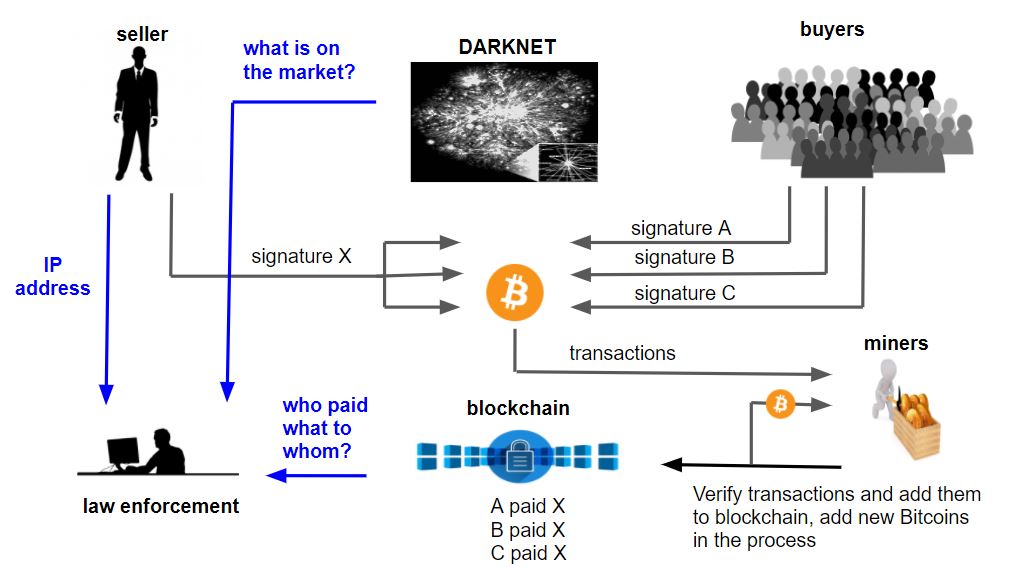





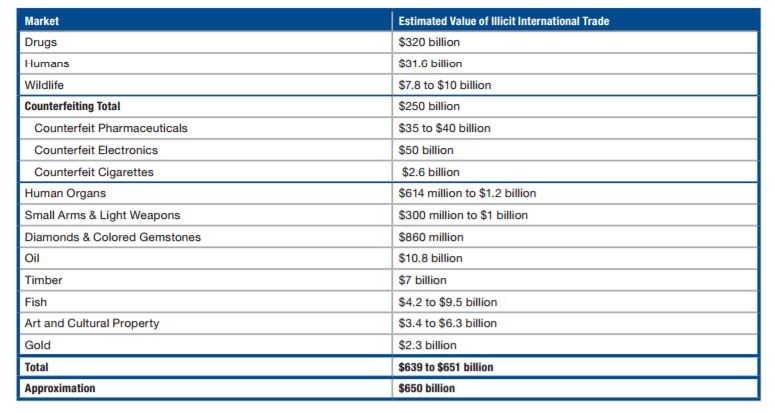 (Source: Transnational Crime In The Developing World February 2011 by GIF)
(Source: Transnational Crime In The Developing World February 2011 by GIF)